Create an NSG based Experiment Manually
In this lab, I will walk you thought the process of manually creating all the resources needed to for an Experiment that allows you to trigger an NSG Fault. Depending on the fault type, the perminssions and roles needed to run the experiment will vary.
Requirements
- Completed all the steps outlined in the Prerequesites section to ensure Chaos Studio is properly setup. For details click here.
Create a Resource group for our Experiment
-
Sign in to Azure portal
-
Select resource groups, then click create
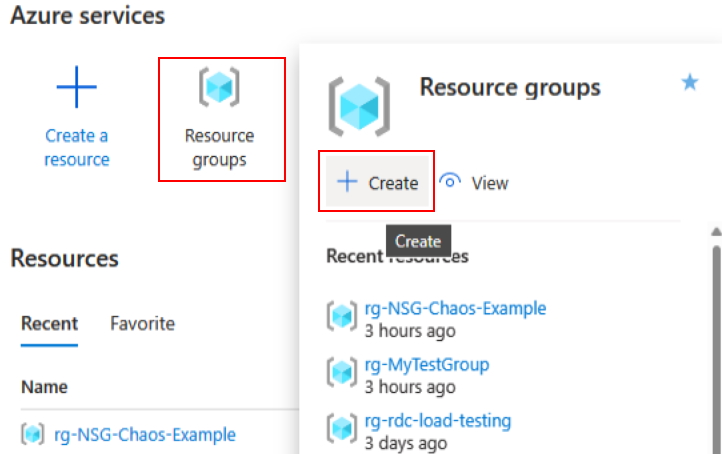 For the Resouce Group name, I used rg-NSG-Chaos-Lab1, I’d suggest you do the same as I will be using this resouce group in other exercises.
For the Resouce Group name, I used rg-NSG-Chaos-Lab1, I’d suggest you do the same as I will be using this resouce group in other exercises. -
Select subscription and enter values and finish creating the Resource Group and use rg-NSG-Chaos-Lab1 for the Resource Group name.
Create a new Network Security Group in the Resouce Group you just created
Note make sure you are NOT creating a (Classic) Network Security Group
-
Navigate to the Azure Portal and search for Network Security Groups and click on *Create and finish the creation using the following properties:
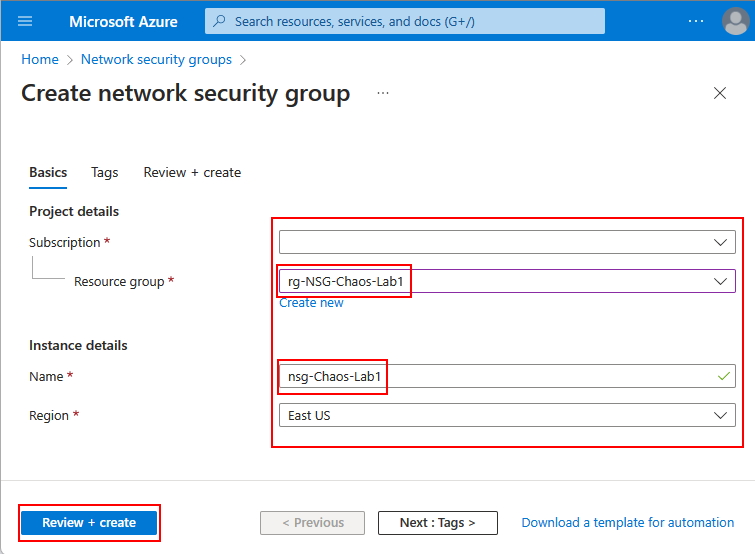
Note how I used nsg-Chaos-Lab1 for the NSG name and I selected the rg-NSG-Chaos-Lab1 resource group we created in the previous step.
Now we need to enable the NSG as target and enable the capabilities for it Capability
-
Navigate the the Azure Portal and search for Chaos Studio and open it
-
Click on Targets and you will see a list of resouces that we can enable.
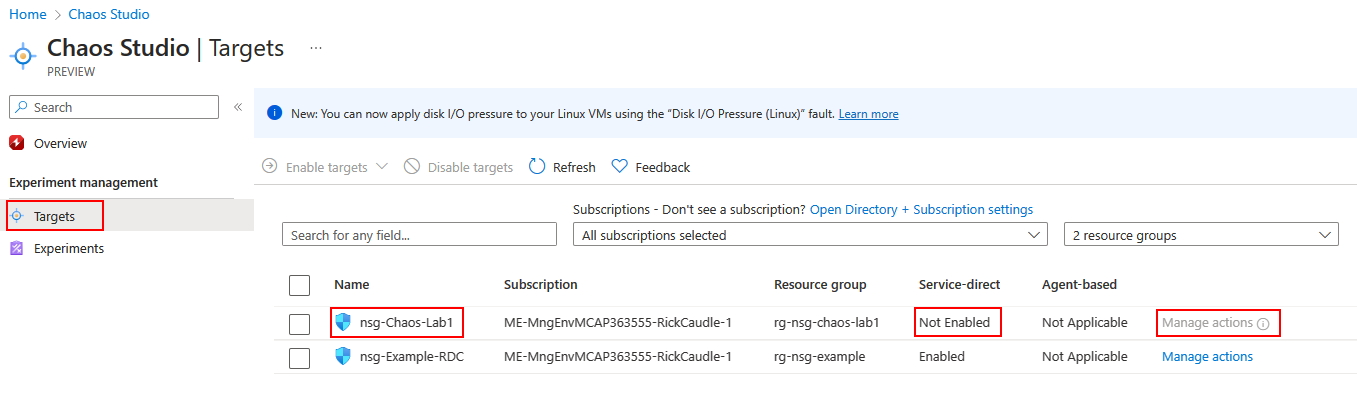
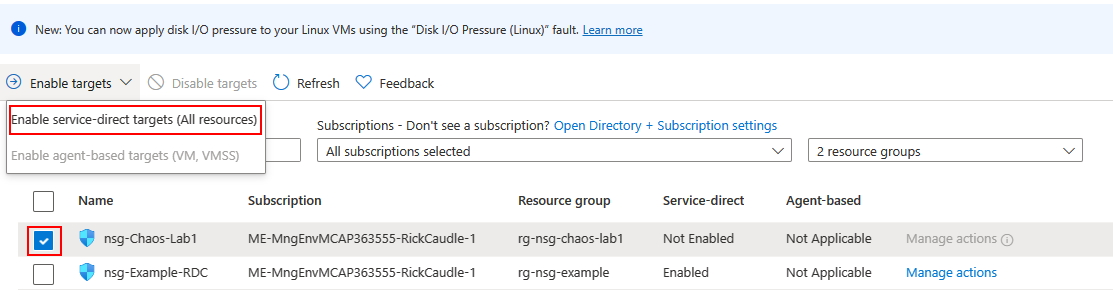
Note that for nsg-Chaos-Lab1 it displays Not Enabled in the Service Direct column and Manage Actions is disabled? This is very important to make note of, if the proper targets/capabilities are not enabled you are going to have issues. Notice for nsg-Chaos-Lab1 it displays Enabled in the Service Direct column and Manage Actions is enabled? Now, we need to do this for the nsg-Chaos-Lab1.
-
Click on nsg-Chaos-Lab1 and make sure it is selected and it is checked, then click on Enable service-direct targets, then click on Review+Enable then click on Enabled
-
Now, refresh the page and Manage Actions will be enabled, click on it. You will note that two Capabilities are selected, now click on Save
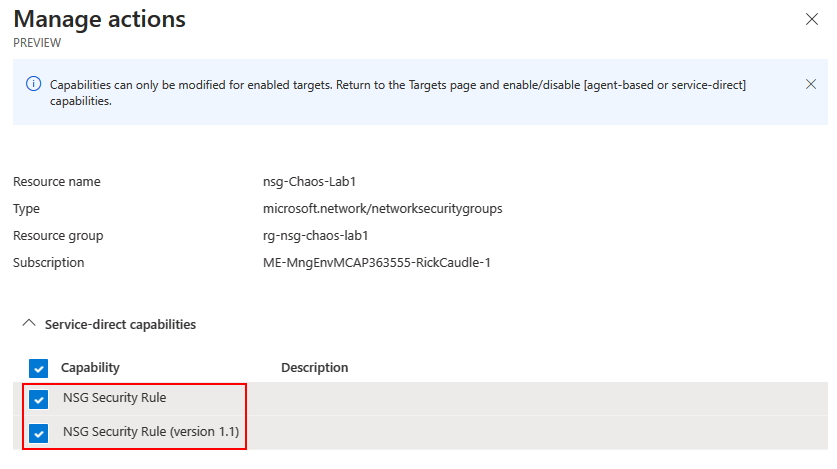
Note now the the NSG target and capabilities are enabled, we can create the Experiment.
Now, lets create an Experiment that introduces an NSG Fault for Service Bus
-
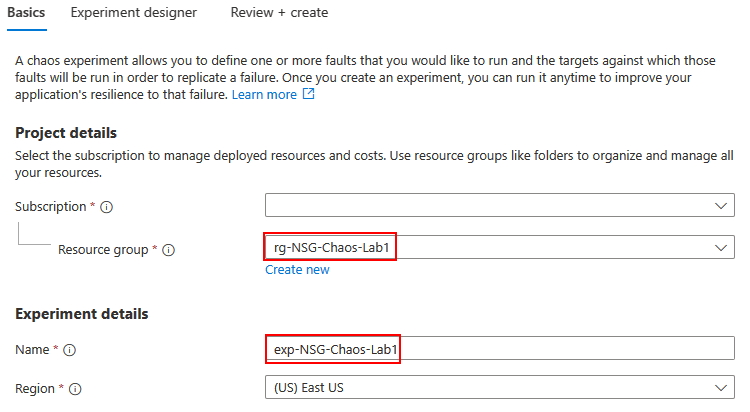
Click on Experiments, then click on Create and populate the Project Details with the following values:
-
Click on Review+Create, then click on Experiment Designer, click on Add Action -> Add Fault and select NSG Security Rule (version 1.1) from the list of faults and set the destinationAddresses to ServiceBus.

-
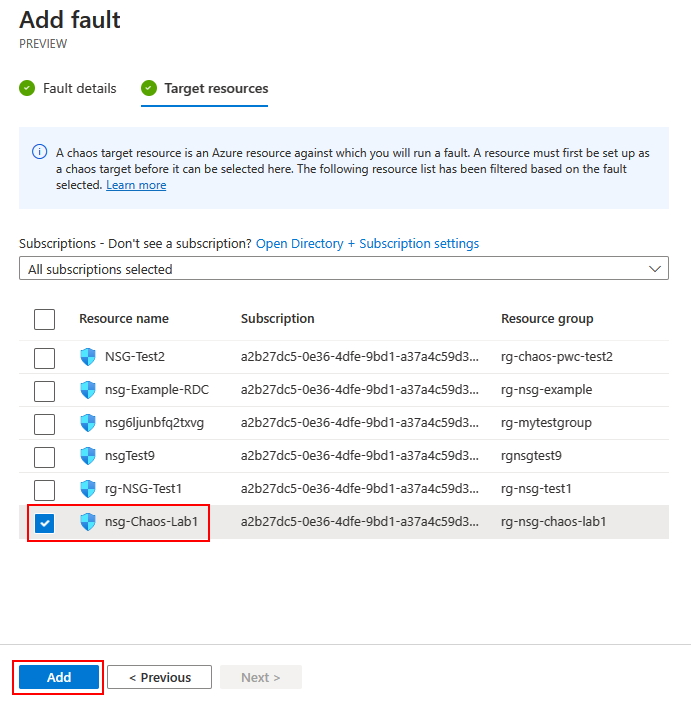
Now, click on Next: Target resources > and check nsg-Chaos-Lab1 and click on Add.
-
Let’s finish up by clicking on Review + Create, then Create. Now, you will see your Experiment in the list of Experiments in Chaos Studio
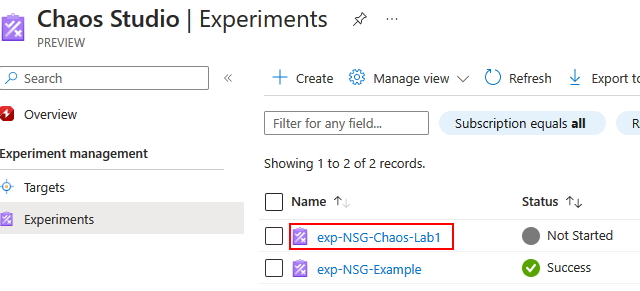
What happens if you run the experiement now?
Did the experiement fail? Why did it fail? Hint: The Experiment uses a System Assigned Identity. Take a look at the error details for the failure. Also, take a look at the role assignments for the experiment. Is there anything missing? Have you looked at the role assignments for the NSG? 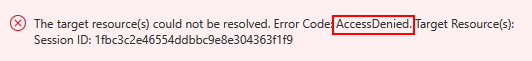
What might you do to fix this? Hint: In order to add a rule to an NSG what role assignment is needed? Do some research and try to figure this out without looking at the answer below. If you want the fix for the issue, click on the Answer for details.
Answer
You need to grant the experiment Network Contributor permissions to the NSG. Navigate to the NSG and and Add the role assignment for Network Contributor and make sure you add exp-NSG-Chaos-Lab1 as a member.Here is what the NSG should look like if you properly added the role assignment: 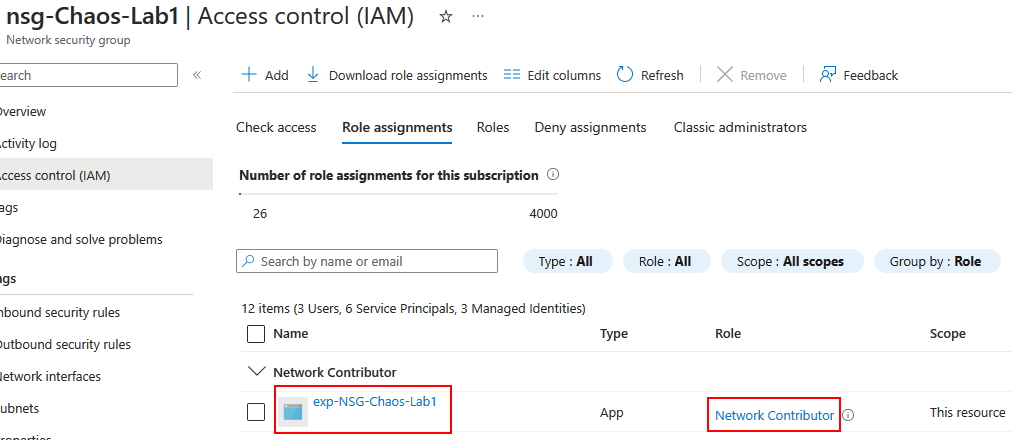
Run the Experiment now that we have added the proper Role Assignment
-
Navigate to the exp-NSG-Chaos-Lab1 experiment and click Start. Keep an eye on the *Status, if you properly add the role assignment, the experiment should change to *Running status.
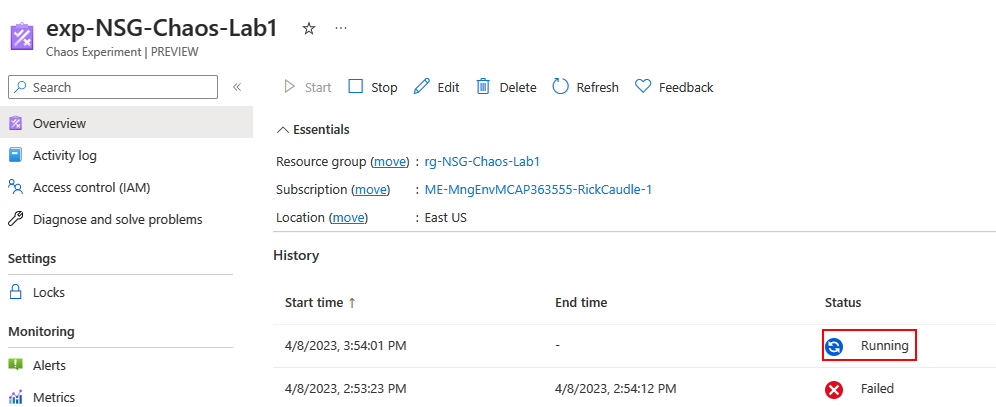
-
Now, navigate to the nsg-Chaos-Lab1, you will see that a new rule called DenyAllOutbound has been added and it’s denying traffic to ServiceBus!

Congratulations!
You have just completed your first Chaos Studio Experiement that leverages an NSG Fault that Denies Service Bus Traffic
Let’s recap the important takeaways for this lab.
- Experiments have a System Assigned Identity and each experiement needs to have the proper role assignments in order to run.
- In this case, the experiement needed to be granted the *Network Contributor role to the Network Security Group.
- When the experiement runs, it will create a rule that denies traffic to range of IP addresses. In order for the experiement to be able to create the Rule it needs Network Contributor to do this.
Recap of the steps needed
- Create a Resource Group to be used for the Experiement and NSG
- Enable the Target/Capibilities for the NSG
- Add the proper Role Assignment
These are the fundamental steps needed for service-direct faults and depending on the fault your role assignements may vary.